Sometimes we become so selfish to be only involved in our daily chorus to be someone, to scale never ending heights of success.
Today while going through my usual habit of scanning the news items, I came across this link, which made me sit up and think… where is our nation heading now a days.
I will just be adding the caption, do read it.
On November 18, 1962, 114 soldiers of the 13th Kumaon fought till the last man, and last bullet, in sub-zero temperatures, to beat back the huge Chinese army.
The Rezang La memorial is a simple marble pillar with names of all the 114 martyrs etched on two sides, in Hindi and in English. The third side has these inspiring words:
How can a Man die better than facing Fearful Odds,For the Ashes of His Fathers and the Temples of His Gods,To the sacred memory of the Heroes of Rezang La,114 Martyrs of 13 Kumaon who fought to the Last Man,Last Round, Against Hordes of Chinese on 18 November 1962.Built by All Ranks 13th Battalion, The Kumaon Regiment.
Monday, November 24, 2008
Wednesday, October 15, 2008
The Bubble Anecdote -- on Land/Stock crisis !
It describes how an 'asset bubble' builds up and what are its consequences. Read it even if it confuses you a bit… things will be clear as you reach the end…
Once there was a little island country. The land of this country was the tiny island itself. The total money in circulation was 2 dollars as there were only two pieces of 1 dollar coins circulating around.
1. There were 3 citizens living on this island country. "A" owned the land. "B" and "C" each owned 1 dollar.
2. "B" decided to purchase the land from "A" for 1 dollar. So, "A" and "C" now each own 1 dollar while "B" owned a piece of land that is worth 1 dollar.
The net asset of the country = 3 dollars.
3. "C" thought that since there is only one piece of land in the country and land is non producible asset, its value must definitely go up. So, he borrowed 1 dollar from "A" and together with his own 1 dollar, he bought the land from "B" for 2 dollars.
"A" has a loan to "C" of 1 dollar, so his net asset is 1 dollar.
"B" sold his land and got 2 dollars, so his net asset is 2 dollars.
"C" owned the piece of land worth 2 dollars but with his 1 dollar debt to "A", his net asset is 1 dollar.
The net asset of the country = 4 dollars.
4. "A" saw that the land he once owned has risen in value. He regretted selling it. Luckily, he has a 1 dollar loan to "C". He then borrowed 2 dollars from "B" and acquired the land back from "C" for 3 dollars. The payment is by
2 dollars cash (which he borrowed) and cancellation of the 1 dollar loan to "C".
As a result, "A" now owned a piece of land that is worth 3 dollars. But since he owed "B" 2 dollars, his net asset is 1 dollar.
"B" loaned 2 dollars to "A". So his net asset is 2 dollars.
"C" now has the 2 coins. His net asset is also 2 dollars.
The net asset of the country = 5 dollars. A bubble is building up.
5. "B" saw that the value of land kept rising. He also wanted to own the land. So he bought the land from "A" for 4 dollars. The payment is by borrowing 2 dollars from "C" and cancellation of his 2 dollars loan to "A".
As a result, "A" has got his debt cleared and he got the 2 coins. His net asset is 2 dollars. "B" owned a piece of land that is worth 4 dollars but since he has a debt of 2 dollars with "C", his net asset is 2 dollars.
"C" loaned 2 dollars to "B", so his net asset is 2 dollars.
The net asset of the country = 6 dollars. Even though, the country has only one piece of land and 2 dollars in circulation.
6. Everybody has made money and everybody felt happy and prosperous.
7. One day an evil wind blowed. An evil thought came to "C"'s mind. 'Hey, what if the land price stop going up, how could "B" repay my loan. There are only 2 dollars in circulation, I think after all the land that "B" owns is worth at most 1 dollar only.'
"A" also thought the same.
8. Nobody wanted to buy land anymore. In the end, "A" owns the 2 dollar coins, his net asset is 2 dollars. "B" owed "C" 2 dollars and the land he owned which he thought worth 4 dollars is now 1 dollar. His net asset become -1 dollar.
"C" has a loan of 2 dollars to "B". But it is a bad debt. Although his net asset is still 2 dollar, his heart is palpitating.
The net asset of the country = 3 dollars again.
Who has stolen the 3 dollars from the country?
Of course, before the bubble burst "B" thought his land worth 4 dollars.
Actually, right before the collapse, the net asset of the country was 6 dollars on papers. His net asset is still 2 dollar, his heart is palpitating.
The net asset of the country = 3 dollars again.
9. "B" had no choice but to declare bankruptcy. "C" has to relinquish his 2 dollars bad debt to "B" but in return he acquired the land which is worth 1 dollar now.
"A" owns the 2 coins, his net asset is 2 dollars. "B" is bankrupt, his net asset is 0 dollar. ("B" lost everything) "C" got no choice but end up with a land worth only 1 dollar ("C" lost one dollar) The net asset of the country = 3 dollars.
There is however a redistribution of wealth.
END OF THE ANECDOTE
"A" is the winner, "B" is the loser, "C" is lucky that he is spared.
ANALYSIS TIME
Once there was a little island country. The land of this country was the tiny island itself. The total money in circulation was 2 dollars as there were only two pieces of 1 dollar coins circulating around.
1. There were 3 citizens living on this island country. "A" owned the land. "B" and "C" each owned 1 dollar.
2. "B" decided to purchase the land from "A" for 1 dollar. So, "A" and "C" now each own 1 dollar while "B" owned a piece of land that is worth 1 dollar.
The net asset of the country = 3 dollars.
3. "C" thought that since there is only one piece of land in the country and land is non producible asset, its value must definitely go up. So, he borrowed 1 dollar from "A" and together with his own 1 dollar, he bought the land from "B" for 2 dollars.
"A" has a loan to "C" of 1 dollar, so his net asset is 1 dollar.
"B" sold his land and got 2 dollars, so his net asset is 2 dollars.
"C" owned the piece of land worth 2 dollars but with his 1 dollar debt to "A", his net asset is 1 dollar.
The net asset of the country = 4 dollars.
4. "A" saw that the land he once owned has risen in value. He regretted selling it. Luckily, he has a 1 dollar loan to "C". He then borrowed 2 dollars from "B" and acquired the land back from "C" for 3 dollars. The payment is by
2 dollars cash (which he borrowed) and cancellation of the 1 dollar loan to "C".
As a result, "A" now owned a piece of land that is worth 3 dollars. But since he owed "B" 2 dollars, his net asset is 1 dollar.
"B" loaned 2 dollars to "A". So his net asset is 2 dollars.
"C" now has the 2 coins. His net asset is also 2 dollars.
The net asset of the country = 5 dollars. A bubble is building up.
5. "B" saw that the value of land kept rising. He also wanted to own the land. So he bought the land from "A" for 4 dollars. The payment is by borrowing 2 dollars from "C" and cancellation of his 2 dollars loan to "A".
As a result, "A" has got his debt cleared and he got the 2 coins. His net asset is 2 dollars. "B" owned a piece of land that is worth 4 dollars but since he has a debt of 2 dollars with "C", his net asset is 2 dollars.
"C" loaned 2 dollars to "B", so his net asset is 2 dollars.
The net asset of the country = 6 dollars. Even though, the country has only one piece of land and 2 dollars in circulation.
6. Everybody has made money and everybody felt happy and prosperous.
7. One day an evil wind blowed. An evil thought came to "C"'s mind. 'Hey, what if the land price stop going up, how could "B" repay my loan. There are only 2 dollars in circulation, I think after all the land that "B" owns is worth at most 1 dollar only.'
"A" also thought the same.
8. Nobody wanted to buy land anymore. In the end, "A" owns the 2 dollar coins, his net asset is 2 dollars. "B" owed "C" 2 dollars and the land he owned which he thought worth 4 dollars is now 1 dollar. His net asset become -1 dollar.
"C" has a loan of 2 dollars to "B". But it is a bad debt. Although his net asset is still 2 dollar, his heart is palpitating.
The net asset of the country = 3 dollars again.
Who has stolen the 3 dollars from the country?
Of course, before the bubble burst "B" thought his land worth 4 dollars.
Actually, right before the collapse, the net asset of the country was 6 dollars on papers. His net asset is still 2 dollar, his heart is palpitating.
The net asset of the country = 3 dollars again.
9. "B" had no choice but to declare bankruptcy. "C" has to relinquish his 2 dollars bad debt to "B" but in return he acquired the land which is worth 1 dollar now.
"A" owns the 2 coins, his net asset is 2 dollars. "B" is bankrupt, his net asset is 0 dollar. ("B" lost everything) "C" got no choice but end up with a land worth only 1 dollar ("C" lost one dollar) The net asset of the country = 3 dollars.
There is however a redistribution of wealth.
END OF THE ANECDOTE
"A" is the winner, "B" is the loser, "C" is lucky that he is spared.
ANALYSIS TIME
Few points worth noting:
- When a bubble is building up, the debt of individual in a country to one another is also building up.
- This story of the island is a close system whereby there is no other country and hence no foreign debt. The worth of the asset can only be calculated using the island's own currency. Hence, there is no net loss.
- An over damped system is assumed when the bubble burst, meaning the land's value did not go down to below 1 dollar.
- When the bubble burst, the fellow with cash is the winner. The fellows having the land or extending loan to others are the loser. The asset could shrink or in worst case, they go bankrupt.
- If there is another citizen "D" either holding a dollar or another piece of land but he refrained to take part in the game, he will, at the end of the day, neither win nor lose. But he will see the value of his money or land go up and down like a see-saw.
- When the bubble was in the growing phase, everybody made money.
- If you are smart and know that you are living in a growing bubble, it is worthwhile to borrow money (like "A") and take part in the game. But you must know when you should change everything back to cash.
- Instead of land, the above applies to stocks as well.
- The actual worth of land or stocks depend largely on psychology.
Labels:
Asset Bubble,
Debt,
Economy,
Land/Stock crisis,
Loan,
Recession
Wednesday, July 23, 2008
Friday, May 30, 2008
Is it Blackout for BlackBerry in India?
The department of telecom (DoT) is learnt to have issued an ultimatum to Canada’s RIM, the maker of the BlackBerry smartphone, that it will have to provide monitoring solutions either in the form of encryption keys, or by shifting servers to India, if it wants to continue operations.
In simple terms "Open code or shut shop".
more details here..
In simple terms "Open code or shut shop".
more details here..
Wednesday, May 28, 2008
Lot More to Do with Webcam with Free Tools

Webcam along with a computer can be used for lot more things apart from video/web chatting.
You will be surprised at the amazing things which can be achieved using a webcam and some free utilities.
A few are mentioned Below :
1. Keep In Touch with Friends and Family
2. Turn Your Webcam into a Motion-Sensing Security Camera
3. Login to Windows with Your Face
4. Snap Pictures of Would-Be Thieves
5. Create Time-Lapse Videos
6. Turn Your PC Into a Photo Booth
7. Chronicle Your Face
8. Document the Weather
9. Set Up a Birdfeeder Webcam
10. Repurpose Your Cell Phone as a Webcam
Details of how to work it out are here.....
Tuesday, May 20, 2008
Refactoring: Improving the Design of Existing Code by Martin Fowler
I liked the below quote from Steve Yegge's blog ..................
When I read this book for the first time, in October 2003, I felt this horrid cold feeling, the way you might feel if you just realized you've been coming to work for 5 years with your pants down around your ankles. I asked around casually the next day: "Yeah, uh, you've read that, um, Refactoring book, of course, right? Ha, ha, I only ask because I read it a very long time ago, not just now, of course." Only 1 person of 20 I surveyed had read it. Thank goodness all of us had our pants down, not just me.

So, I started reading it ... Don't want to keep my pants down around ankles anymore.
When I read this book for the first time, in October 2003, I felt this horrid cold feeling, the way you might feel if you just realized you've been coming to work for 5 years with your pants down around your ankles. I asked around casually the next day: "Yeah, uh, you've read that, um, Refactoring book, of course, right? Ha, ha, I only ask because I read it a very long time ago, not just now, of course." Only 1 person of 20 I surveyed had read it. Thank goodness all of us had our pants down, not just me.

So, I started reading it ... Don't want to keep my pants down around ankles anymore.
Thursday, May 15, 2008
Tuesday, May 13, 2008
Data from Hubble cheaper than (SMS)texting
A British space scientist has worked out that sending texts via mobile phones works out to be far more expensive than downloading data from the Hubble Space Telescope.

 Calculations made by the University of Leicester's expert Nigel Bannister, who worked out the cost of obtaining a megabyte of data from Hubble and compared that with the five pence cost of sending a text, were used for the Channel 4 Dispatches programme 'The Mobile Phone Rip-Off'.
Calculations made by the University of Leicester's expert Nigel Bannister, who worked out the cost of obtaining a megabyte of data from Hubble and compared that with the five pence cost of sending a text, were used for the Channel 4 Dispatches programme 'The Mobile Phone Rip-Off'.
The maximum size for a text message is 160 characters, which takes 140 bytes because there are only seven bits per character in the text messaging system, and we assume the average price for a text message is 5 pence."
"There are 1,048,576 bytes in a megabyte, so that's one million/140 = 7490 text messages to transmit one megabyte. At 5 pence each, that's £374.49 per MB or about 4.4 times more expensive than the 'most pessimistic' estimate for Hubble Space Telescope (HST) transmission costs."
He said it had been difficult to work out exactly how much Hubble data transmission costs. So, he contacted Nasa who gave him a firm figure of £8.85 per megabyte (MB) for the transmission of data from HST to the Earth.
"This doesn't include the cost of the ground stations and the time of the personnel along the way, but it is an unambiguous number for that part of the process."

 Calculations made by the University of Leicester's expert Nigel Bannister, who worked out the cost of obtaining a megabyte of data from Hubble and compared that with the five pence cost of sending a text, were used for the Channel 4 Dispatches programme 'The Mobile Phone Rip-Off'.
Calculations made by the University of Leicester's expert Nigel Bannister, who worked out the cost of obtaining a megabyte of data from Hubble and compared that with the five pence cost of sending a text, were used for the Channel 4 Dispatches programme 'The Mobile Phone Rip-Off'.
Bannister said: "The bottom line is texting is at least four times more expensive than transmitting data from Hubble, and is likely to be substantially more than that.
The maximum size for a text message is 160 characters, which takes 140 bytes because there are only seven bits per character in the text messaging system, and we assume the average price for a text message is 5 pence."
"There are 1,048,576 bytes in a megabyte, so that's one million/140 = 7490 text messages to transmit one megabyte. At 5 pence each, that's £374.49 per MB or about 4.4 times more expensive than the 'most pessimistic' estimate for Hubble Space Telescope (HST) transmission costs."
He said it had been difficult to work out exactly how much Hubble data transmission costs. So, he contacted Nasa who gave him a firm figure of £8.85 per megabyte (MB) for the transmission of data from HST to the Earth.
"This doesn't include the cost of the ground stations and the time of the personnel along the way, but it is an unambiguous number for that part of the process."
Friday, May 9, 2008
A PRE-SCHOOL TEST FOR YOU
A PRE-SCHOOL TEST FOR YOU
Which way is the bus below travelling?
To the left or to the right?
They answered:"Because you can't see the door to get on the bus."

Which way is the bus below travelling?
To the left or to the right?
Can't make up your mind?Look carefully at the picture again.
Still don't know?
. . . . . . .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. Primary school children were shown this picture and asked the same question.
90% of them gave this answer:
"The bus is travelling to the right.."
They answered:"Because you can't see the door to get on the bus."
How do you feel now???

Thursday, May 8, 2008
An Interview with Bjarne Stroustrup
C++ creator Bjarne Stroustrup discusses the evolving C++0x standard, the education of programmers, and the future of programming.
Very Interesting article, check it out....
Very Interesting article, check it out....
Tuesday, May 6, 2008
Wednesday, April 23, 2008
Virtual Sticky Notes for a Neat Desktop
It’s paperless!
Well, if you happen to be one of those who love a neat desktop or the environment, then you could have a go at trying virtual sticky notes.
These are software applications that allow you to put a note on your display just as you would a Word document or presentation---no paper, no gum, and you can get rid of them by just hitting the ‘delete’ button.
There are a number of options (paid and free) available, but one of the most popular is Zhorn Software’s Stickies. It is a mere 950 KB download (from http:// http://%20www.zhornsoftware.co.u%20k/stickies/download.html ), installs smoothly on all versions of Windows, and is free.
Once installed, Stickies parks itself in the QuickLaunch bar. If you want to put a new Stickie, just double click on the Stickies icon and start typing your message on the Sticky that pops up. If you want to look at older ones or tweak configurations, go for a right click.
You can have all kinds of fonts and skins from the traditional yellow to shocking pink, if such is your inclination. Also tweak able is just how opaque you want the Stickies to be and whether you want them to always be visible or disappear the moment you click outside them.
And of course, unlike traditional sticky notes which restrict you to a pitiful scrap of paper, here you can make the Sticky as large as you wish!
It's more than just sticky business
These Stickies also do stuff that the normal paper ones cannot. For instance, you can tag them to a particular document or file, so that they show up only when that particular document of file is opened. You can also send them across to other people over the local area network or by using email.
You can even use them as alarms, asking them to pop up at a certain time say, as a reminder for an appointment. You can even transfer Stickies to handheld devices, provided they run Pocket PC and Palm OS. What’s more, Stickies is supposed to be a relatively safe piece of software.
Well, if you happen to be one of those who love a neat desktop or the environment, then you could have a go at trying virtual sticky notes.
These are software applications that allow you to put a note on your display just as you would a Word document or presentation---no paper, no gum, and you can get rid of them by just hitting the ‘delete’ button.
There are a number of options (paid and free) available, but one of the most popular is Zhorn Software’s Stickies. It is a mere 950 KB download (from http:// http://%20www.zhornsoftware.co.u%20k/stickies/download.html ), installs smoothly on all versions of Windows, and is free.
Once installed, Stickies parks itself in the QuickLaunch bar. If you want to put a new Stickie, just double click on the Stickies icon and start typing your message on the Sticky that pops up. If you want to look at older ones or tweak configurations, go for a right click.
You can have all kinds of fonts and skins from the traditional yellow to shocking pink, if such is your inclination. Also tweak able is just how opaque you want the Stickies to be and whether you want them to always be visible or disappear the moment you click outside them.
And of course, unlike traditional sticky notes which restrict you to a pitiful scrap of paper, here you can make the Sticky as large as you wish!
It's more than just sticky business
These Stickies also do stuff that the normal paper ones cannot. For instance, you can tag them to a particular document or file, so that they show up only when that particular document of file is opened. You can also send them across to other people over the local area network or by using email.
You can even use them as alarms, asking them to pop up at a certain time say, as a reminder for an appointment. You can even transfer Stickies to handheld devices, provided they run Pocket PC and Palm OS. What’s more, Stickies is supposed to be a relatively safe piece of software.
Tuesday, April 8, 2008
Importing old email to Gmail.
Got a new Gmail ID? But wondering how you can transfer your old mails from your other accounts to it?
Here are a few tips by which you can actually make it happen.
First, you need to tell Gmail how to retrieve your mail from old accounts using POP. For this you need to set up a Mail Fetcher.
* Click Settings from the top of any email page.
* Click Accounts.
* In the Get mail from other accounts section, click Add another mail account.
* Enter the full email address of the account you'd like to access, then click
* Google will populate the Username and POP Server fields when possible, based on your email address. Enter your Password.
Now decide whether to:
* Leave a copy of retrieved messages on the server
* Label incoming messages
* Archive incoming messages
If you'd like to keep a copy of each message Gmail retrieves in your other mail accounts, select the Leave a copy of retrieved messages on the server checkbox. This way, you can access mail in your other accounts, and in Gmail.
Please note that some email services may still delete your messages when Gmail fetches them. If this option is checked, Gmail will instruct the other domain to leave the messages in place, though the final behavior is up to the other domain. If you'd rather delete copies of messages that Gmail retrieves, leave this option unchecked. Gmail will delete the messages from the other account as those messages are retrieved, meaning you'll only be able to read them in Gmail.
Make sure that you always use a secure connection (SSL) when retrieving mail. If the email account being retrieved from supports Secure Sockets Layer (SSL) encryption, you can select this option to have all information sent through a secured connection. If you select this option, and your email provider doesn't support it, Gmail will let you know that your configuration failed.
Clicking Show error details will likely reveal a Protocol error in this case. You'll need to uncheck this selection before continuing.
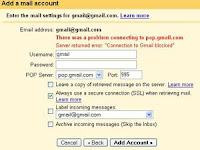 If you'd like to automatically label all messages that are retrieved from your non-Google account, select this option.
If you'd like to automatically label all messages that are retrieved from your non-Google account, select this option.
You can choose to use the predefined label (your email address), or you can select an existing label or create a new one from the drop-down list.
Archiving moves messages out of your inbox and into All Mail, letting you tidy up your inbox without deleting anything.
Messages you archive can be found in All Mail, in any labels you've applied, and by searching Gmail. When someone responds to a message you've archived, the conversation containing that message will reappear in your inbox.
Here's how you can archive messages:
* Select a message by checking the box next to the sender's name.
* Click Archive.
* If you have a conversation open, you can archive it by clicking Archive at the top of the page.
To move mail back to your inbox:
* Click All Mail.
* Check the box next to the sender's name.
* Click Move to Inbox.
Go to Settings > Accounts > Get mail from other accounts > Add another mail account.
A new window will pop-up asking you for the email address you're going to import mail from. Fill this in and click on "Next Step." It is useful to label incoming messages with "Imported" (use any thoughtful label you can think of), so that you could easily identify imported mail later on.
If you would still like to have the option of sending mail from Gmail that appears to recipients as if it were sent from your old email address, you can set up a custom "From:" by going to Settings > Accounts > Send mail as: > Add another email address.
Click on "Next Step" and then "Send Verification."
You'll receive an email with instructions on how to validate your old address. Once it is set up you can select this address in the "From" field when replying or forwarding.
Then, validate with "Add Account" and finally, select "Yes, I want to be able to send mail as yourname@gmail.com."
Courtesy: Google
Here are a few tips by which you can actually make it happen.
First, you need to tell Gmail how to retrieve your mail from old accounts using POP. For this you need to set up a Mail Fetcher.
* Click Settings from the top of any email page.
* Click Accounts.
* In the Get mail from other accounts section, click Add another mail account.
* Enter the full email address of the account you'd like to access, then click
* Google will populate the Username and POP Server fields when possible, based on your email address. Enter your Password.
Now decide whether to:
* Leave a copy of retrieved messages on the server
* Label incoming messages
* Archive incoming messages
If you'd like to keep a copy of each message Gmail retrieves in your other mail accounts, select the Leave a copy of retrieved messages on the server checkbox. This way, you can access mail in your other accounts, and in Gmail.
Please note that some email services may still delete your messages when Gmail fetches them. If this option is checked, Gmail will instruct the other domain to leave the messages in place, though the final behavior is up to the other domain. If you'd rather delete copies of messages that Gmail retrieves, leave this option unchecked. Gmail will delete the messages from the other account as those messages are retrieved, meaning you'll only be able to read them in Gmail.
Make sure that you always use a secure connection (SSL) when retrieving mail. If the email account being retrieved from supports Secure Sockets Layer (SSL) encryption, you can select this option to have all information sent through a secured connection. If you select this option, and your email provider doesn't support it, Gmail will let you know that your configuration failed.
Clicking Show error details will likely reveal a Protocol error in this case. You'll need to uncheck this selection before continuing.
 If you'd like to automatically label all messages that are retrieved from your non-Google account, select this option.
If you'd like to automatically label all messages that are retrieved from your non-Google account, select this option.You can choose to use the predefined label (your email address), or you can select an existing label or create a new one from the drop-down list.
Archiving moves messages out of your inbox and into All Mail, letting you tidy up your inbox without deleting anything.
Messages you archive can be found in All Mail, in any labels you've applied, and by searching Gmail. When someone responds to a message you've archived, the conversation containing that message will reappear in your inbox.
Here's how you can archive messages:
* Select a message by checking the box next to the sender's name.
* Click Archive.
* If you have a conversation open, you can archive it by clicking Archive at the top of the page.

To move mail back to your inbox:
* Click All Mail.
* Check the box next to the sender's name.
* Click Move to Inbox.

Go to Settings > Accounts > Get mail from other accounts > Add another mail account.
A new window will pop-up asking you for the email address you're going to import mail from. Fill this in and click on "Next Step." It is useful to label incoming messages with "Imported" (use any thoughtful label you can think of), so that you could easily identify imported mail later on.

If you would still like to have the option of sending mail from Gmail that appears to recipients as if it were sent from your old email address, you can set up a custom "From:" by going to Settings > Accounts > Send mail as: > Add another email address.
Click on "Next Step" and then "Send Verification."
You'll receive an email with instructions on how to validate your old address. Once it is set up you can select this address in the "From" field when replying or forwarding.
Then, validate with "Add Account" and finally, select "Yes, I want to be able to send mail as yourname@gmail.com."
Courtesy: Google
Tuesday, April 1, 2008
Detect Heap Corruption -- Using CrtCheckMemory()
To debug code that caused heap corruption,We normally do struggle against the computer in order to understand what causes the corruption and how.
In the search for memory validation APIs I have found _CrtCheckMemory() API which is being used by debug version of C run-time libraries. Using this API wrapped with an assert macro gives us the opportunity to check the heap every few lines of code without any overhead in release version: _ASSERTE( CrtCheckMemory());
it would be smart idea to use it even without any visible corruption, it saves time in the long run . This tip is based on information written on the MSDN.
In the search for memory validation APIs I have found _CrtCheckMemory() API which is being used by debug version of C run-time libraries. Using this API wrapped with an assert macro gives us the opportunity to check the heap every few lines of code without any overhead in release version: _ASSERTE( CrtCheckMemory());
it would be smart idea to use it even without any visible corruption, it saves time in the long run . This tip is based on information written on the MSDN.
Labels:
C++,
CrtCheckMemory(),
Heap corruption,
memory,
MSDN
Tuesday, March 25, 2008
Forcing Cpp Functions To Be Called Non-inlined
Can you think of a way to force a function (usually a very small one) from not being inlined by a compiler for optimization purpose.
Often such little functions are auto-inlined by the optimizer, when compiling in release/optimized mode. Although there is a way to prevent function from inlining by prototyping it with the _cdecl keyword, sometimes all you need just specific calls to be non-inlined.
Here is the macro:
#define NON_INLINED_CALL(a) (((int)(a)+1)?(a):(0))
Now, by forcing some fake calculation (int(a)+1) we stop the compiler from optimizing given line, also by using v ? (a) : (0), we are forcing the compiler to use the _cdecl way of calling the function.
Example:
static int test(int a, int b, int c)
{
return a*b*c;
}
#define NON_INLINED_CALL(a) (((int)(a)+1)?(a):(0))
extern int results[2];
extern int a, b, c;
extern int d, e, f;
void test2( void )
{
results[0] = test(a,b,c); // Eventually with good optimizations this will be inlined
results[1] = NON_INLINED_CALL(test)(d,e,f); // No inlining here
}
Under MSVC we can construct simple and faster macro
#define NON_INLINED_CALL_MSVC(a) ((a) ? (a) : 0)
but the latter will not stop GCC optimizer, and we'll not get the results we wanted to.
P.S. I didn't test any other compilers - only GCC 2.99(ps2-ee one), and MSVC6.00
Often such little functions are auto-inlined by the optimizer, when compiling in release/optimized mode. Although there is a way to prevent function from inlining by prototyping it with the _cdecl keyword, sometimes all you need just specific calls to be non-inlined.
Here is the macro:
#define NON_INLINED_CALL(a) (((int)(a)+1)?(a):(0))
Now, by forcing some fake calculation (int(a)+1) we stop the compiler from optimizing given line, also by using v ? (a) : (0), we are forcing the compiler to use the _cdecl way of calling the function.
Example:
static int test(int a, int b, int c)
{
return a*b*c;
}
#define NON_INLINED_CALL(a) (((int)(a)+1)?(a):(0))
extern int results[2];
extern int a, b, c;
extern int d, e, f;
void test2( void )
{
results[0] = test(a,b,c); // Eventually with good optimizations this will be inlined
results[1] = NON_INLINED_CALL(test)(d,e,f); // No inlining here
}
Under MSVC we can construct simple and faster macro
#define NON_INLINED_CALL_MSVC(a) ((a) ? (a) : 0)
but the latter will not stop GCC optimizer, and we'll not get the results we wanted to.
P.S. I didn't test any other compilers - only GCC 2.99(ps2-ee one), and MSVC6.00
Monday, March 24, 2008
Preventing object creation on stack
In C++, sometimes you don't want the user of your class to create the object of it on stack, because the stack resource is rare. Is there any way to do this?
Yes!!!
What you should do is to make your destructor private, rather than public or protected.
You can do like this:
class CTest {
private:
~CTest ();
}
Why only private, because if you make it protected, yes the object this class can't not be created on stack, but it's derived class can!
Then, if you want to create the object on stack, like
CTest test;
The compiler is gona complain, the error message is most probably like 'CTest::~CTest' : cannot access private member declared in class CTest'.
That's because the compiler will actually check if it can delete the object if it's created on stack, because it's compiler's business to take care of this. If you do like:
CTest* test
or
CTest* test = new CTest
It's gona be fine, because the only thing you put on the stack is just the pointer, compiler don't even have to call the destructor of the pointer.
Then, how do you delete the object whose destructor is private?? Just use delete operator is not going to work, because delete operator is not a part of the CTest class. So you have to provide a function which will delete the object itself.
It's like:
void CTest::Release()
{
delete this;
}
Since "delete this" is not a "good manner"(it works, but it's not recommended), you have to pay more attention when you use this. You have to make sure that the object is not created by "new[]". You have to make sure Release is the last function you call on this object, etc.
Yes!!!
What you should do is to make your destructor private, rather than public or protected.
You can do like this:
class CTest {
private:
~CTest ();
}
Why only private, because if you make it protected, yes the object this class can't not be created on stack, but it's derived class can!
Then, if you want to create the object on stack, like
CTest test;
The compiler is gona complain, the error message is most probably like 'CTest::~CTest' : cannot access private member declared in class CTest'.
That's because the compiler will actually check if it can delete the object if it's created on stack, because it's compiler's business to take care of this. If you do like:
CTest* test
or
CTest* test = new CTest
It's gona be fine, because the only thing you put on the stack is just the pointer, compiler don't even have to call the destructor of the pointer.
Then, how do you delete the object whose destructor is private?? Just use delete operator is not going to work, because delete operator is not a part of the CTest class. So you have to provide a function which will delete the object itself.
It's like:
void CTest::Release()
{
delete this;
}
Since "delete this" is not a "good manner"(it works, but it's not recommended), you have to pay more attention when you use this. You have to make sure that the object is not created by "new[]". You have to make sure Release is the last function you call on this object, etc.
Subscribe to:
Posts (Atom)






